Secure and Seamless Carrier Wi-Fi Services with Passpoint
This is an excerpt from ENEA’s white paper Wi-Fi in the 5G Era – Strategy Guide for Operators. The full white paper is available here if you like what you read. Don’t hesitate to contact ENEA if you have any questions.
In this post, we will talk about the different Passpoint releases (R1-R3) and the status of device support. Don’t miss our upcoming blog post, A Pragmatic Approach to Passpoint on how to overcome challenges with the lack of widespread device support for R2 and R3.
One of the essential tools in the Wi-Fi toolbox is Passpoint® with SIM authentication. It enables seamless and secure carrier-grade quality and highly monetizable Wi-Fi services. The Wi-Fi 6 and Wi-Fi 6E radio technology, capable of delivering high-quality wireless connectivity, is an excellent starting point. But for service providers, such capabilities must be transformed into user-friendly, secure, well-defined, and preferably carrier-class high-speed wireless data services.
To that end, the Wi-Fi industry has developed the Hotspot 2.0 standard, nowadays more commonly referred to by its equipment certification name of Passpoint. Once provisioned on the phone or other Wi-Fi device, Passpoint technology allows users to connect securely, instantly, and automatically to the public (or enterprise) Passpoint-capable Wi-Fi networks, for example, at public venues such as airports, stadiums, transport hubs, on aircraft, and so on.
The Passpoint technology also facilitates roaming onto Wi-Fi networks belonging to other service providers or third parties, given that a roaming agreement with the subscriber’s home service provider exists. The WBA OpenRoaming initiative has the potential to make Wi-Fi roaming just as seamless for the user as roaming with cellular phones.
THE COMPONENTS OF PASSPOINT 
A Passpoint-capable network is defined by supporting the following functions:
- The network (Wi-Fi access point) should broadcast its capabilities and available services using 802.11u and a protocol called ANQP.
- The network must use 802.1x-based authentication and WPA2 or WPA3 for over-the-air encryption.
- Support for EAP-SIM/AKA (SIM identity-based) or EAP-TLS/TTLS (certificate-based methods usually for non-SIM devices) authentication.
- Optional Wi-Fi roaming with home operator billing.
A critical component is the capability of Passpoint services to deliver ‘Wi-Fi offload’-type services based on credentials stored in the subscriber’s SIM. This means mobile operators can integrate carrier Wi-Fi services into their total service offering. Read more about this in our Wi-Fi and Cellular Convergence – Opportunities Today post.
Passpoint is designed to create a carrier-grade Wi-Fi service with a familiar and seamless user experience like that of cellular networks. However, mobile operators can comfortably apply EAP-SIM/AKA authentication and mobile core integration outside the complete Hotspot 2.0/Passpoint specification. Aptilo Networks was already providing such solutions long before the release of the first Passpoint-capable devices. This also means that EAP-based authentication (SIM/AKA and TLS/TTLS) is not equivalent to Passpoint as such, which is a common misunderstanding.
In the USA, Passpoint-capable Wi-Fi services and roaming are fairly readily available, for example, on the Boingo Wi-Fi network deployed at many airport locations and on some public Wi-Fi networks provided by US cablecos, for instance, on the former Time Warner Cable public Wi-Fi network today owned and operated by Charter Communications. Today, both Android and iOS operating systems natively support Passpoint, and many phones provided by US carriers are pre-provisioned to support Passpoint services.
In Europe and elsewhere, Passpoint-capable Wi-Fi services are less common but available from some major carriers in the form of EAP-SIM/AKA enabled ‘Wi-Fi offload’ convergent mobile services. Most enterprise-grade Wi-Fi access points are certified according to the Passpoint specifications.
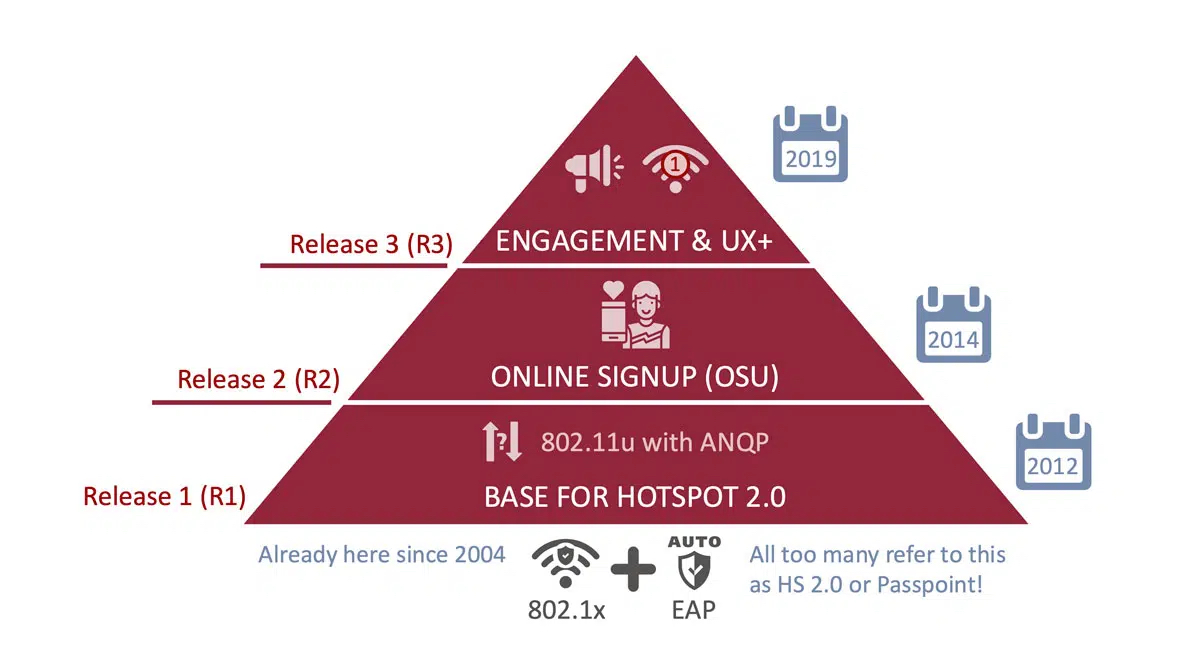
Release 1 (R1)
The first release was introduced in 2012, and all the protocols and standards mentioned above, including 802.11u and ANQP, were included with the ability for the device to discover Passpoint-enabled networks and automatically connect to the optimal one.
Challenges still remain in the onboarding of new devices. Users need to provision Pass-point R1 credentials manually by downloading a particular file that contains profile and credential information. Many service providers use an app to make this process seamless for the user. More or less, all mobile phones and laptops support Passpoint RI. This includes Apple iPhones, although Apple has never formally certified them.
Release 2 (R2)
This version, released in 2014, included the important Online Sign-Up (OSU) server allowing new users to create an account and, in a user-friendly way, provision Passpoint credentials at the point of access. This enables easy ad-hoc sign-up of new users, where they can select the service provider of choice if several options exist. The client validates the OSU server certificate to ensure that the server is trusted. SOAP-XML or OMA-DM messages over HTTPS are then used for secure communications between the client and the provisioning servers.
Passpoint R2 requires a separate SSID for Online Sign-Up, either an open SSID or a so-called OSEN (OSU Server-only Authenticated L2 Encryption Network). This version also includes enhanced policy control for service providers. Device support is still limited.
Release 3 (R3)
R3 was released in 2019, but has not yet been certified by any major handset manufacturers (as of September 2022). This version includes several new ANQP protocol elements and improvements in the interaction between operators and end-users. While previous versions have focused entirely on automatic connection and onboarding of the users, Passpoint R3 aims to enhance captive portal functions by leveraging ANQP messaging.
For the first time, Passpoint allows operators to offer B2B customers a tool to engage with visitors. They can do this through a Venue URL, which displays information about the Wi-Fi service and, at the same time, provides offers and local promotions. The R3 version also includes features for end-users to approve terms and conditions and charges for the Wi-Fi service.
We think Passpoint R3 may have attempted to push the user engagement features too far. Deploying these features through ANQP locally in the access points will make it harder to maintain central control, especially in a multi-vendor deployment scenario. Because of the challenges in management and lack of device support, there is a risk that R3 will never be implemented in carrier Wi-Fi networks.
Passpoint R3 also makes roaming much quicker and easier as the client can indicate its membership of a roaming consortium to a Wi-Fi access point.
Security is further improved in R3 with support up WPA3-Enterprise, whereas R2 and R1 only support up to WPA2-Enterprise. It is also possible to use the same SSID for both the actual Wi-Fi service (WPA2/WPA3) and the online sign-up (OSEN) functionality.
STRATEGIES FOR DEPLOYING PASSPOINT IN THE REAL WORLD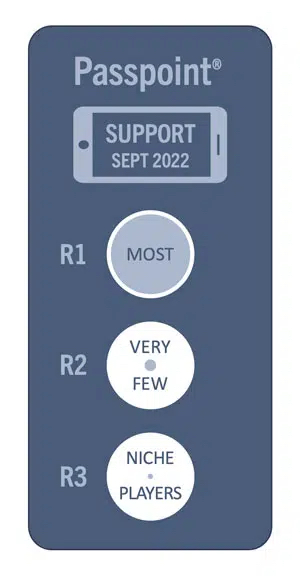
The Passpoint certification is a moving target, and things may have changed by the time you read this. But, as of September 2022, only niche handset brands has been certified for the latest Passpoint release (R3). Some Android-based phones are R2 certified, but many are old and not in the market anymore. In addition, smartphone vendors usually customize the Android platform to match their product requirements. So, just because it works with one vendor doesn’t mean it works with another.
The Passpoint certification from Wi-Fi Alliance only certifies the radio protocols. In practice, new releases from R2 and above, which include more complex service-related features, cannot be guaranteed to work end-to-end in a Wi-Fi service. We have experienced this through the testing conducted by the Wireless Broadband Alliance (WBA).
Conversely, it is probably true that devices with R2 support that has not been Passpoint certified also exist, just as R1 is supported in iPhones without official certification.
But as a service provider, you cannot rely on so many unknown parameters.
On a more positive note, it is generally true that most smartphones, tablets, and laptops now support at least Passpoint R1. Therefore, operators should create and deploy Wi-Fi services based on R1, possibly with an extension for selective use of R2.
One thing is certain: Operators who wait for new standards to be fully deployed and for mobile device manufacturers to adopt them risk waiting for a very long time. It is not only the complexity of the technology that decides whether a handset manufacturer develops support for standards like Passpoint R2/R3 or not. Thus, the wait could go on forever. Fortunately, there is no reason to delay the introduction of carrier-grade Wi-Fi services.
In our upcoming blog post, A Pragmatic Approach to Passpoint, we will discuss how Passpoint R1, together with the new Captive Portal API, may well be the interim solution that, in the end, becomes the permanent pragmatic solution for Passpoint-enabled networks.
